作为站长和开发者,手上的网站或者接口啥的越来越多的对SSL证书有要求,之前一直使用的FreeSSL的证书,前段时间FreeSSL开始强制绑定手机号,便一直在寻找各种免费证书,BuyPass便是到目前为止证书有效期免费时长相对来说比较长的一家,这里分享一下我的使用体验。
免费证书
除了FreeSSL,国内的各大云服务厂商比如说腾讯云、阿里云、七牛云、又拍云等也提供免费1年证书申请,但是这其中绝大多数都需要实名认证,但我还是想找找国外免费的替代服务的,letsencrypt 众所周知没啥好说的,同时支持单域名、多域名及泛域名也就是wildcard,但是不便的地方也有,就是有效期只有三个月,如果是自有服务器还好,配置个定时任务就能搞定,但是域名多或者没法设置定时任务的时候就麻烦了,3个月一次手动改着实有些麻烦。于是我就一直在找是否有证书有效期相对更长一点的,能少一次也少一次。
搜索引擎找了一番之后发现,免费证书大部分都是90天有效时长的,BuyPass算是相对来说有效期更长的,单次颁发最长180天有效期,虽然也不是1年有效,但是多少比letsencrypt长一倍的有效期,而且CA还是国外的,也不需要绑定手机号啥的,直接使用acme.sh脚本就能申请,还是比较简单的。
使用certbot申请BuyPass免费证书
申请之前,如果是单域名并且是将证书用在本机,记得先把域名解析到本地IP。
和letsencrypt一样,使用certbot就能直接申请BuyPass的免费证书,安装certbot之后,在命令行添加BuyPass的服务器地址就能申请到BuyPass的免费证书,比如说:
certbot certonly --server 'https://api.buypass.com/acme/directory'其实和letsencrypt命令差不多,都是使用acme协议,只是使用的不是letsencrypt的证书服务而已。
以我自己的实际申请过程来说,完整的输入及输出如下:
root@cloudbool-buypass:~# certbot certonly --server 'https://api.buypass.com/acme/directory'
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): admin@test.cloudbool.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at https://api.buypass.com/acme/terms/750. You
must agree in order to register with the ACME server at
https://api.buypass.com/acme/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: N
Please enter in your domain name(s) (comma and/or space separated) (Enter 'c'
to cancel): test.cloudbool.com
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for test.cloudbool.com
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/test.cloudbool.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/test.cloudbool.com/privkey.pem
Your cert will expire on 2021-09-07. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-leBuyPass证书使用
证书申请下来之后,配置Nginx等就能直接使用了,如图,这是我申请下来之后配置Nginx使用的截图,域名用的是test.cloudbool.com,有效期确实是180天:
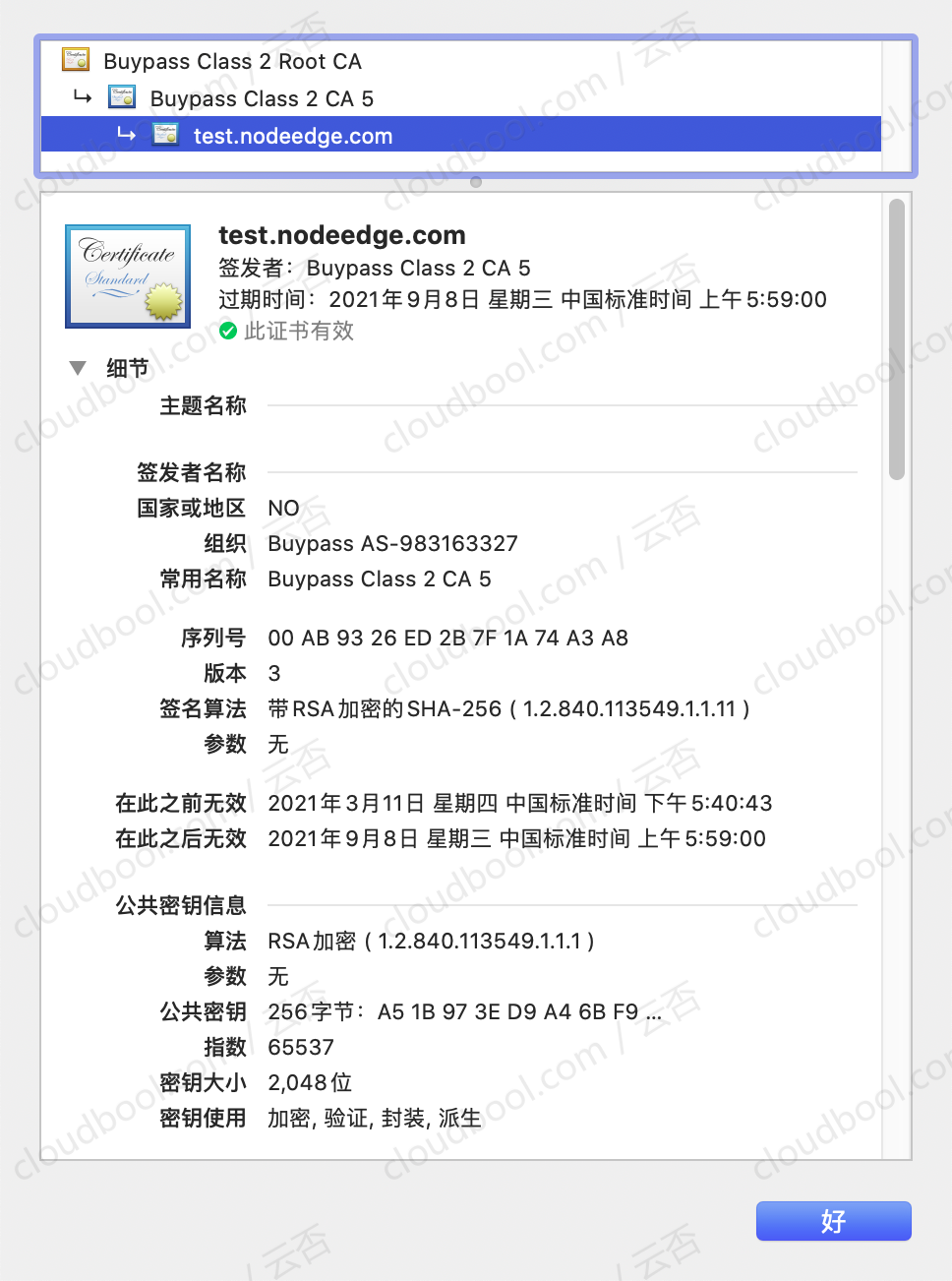
证书信息完整截图如下:
root@cloudbool-buypass:/etc/letsencrypt/live/test.cloudbool.com# openssl x509 -noout -text -in fullchain.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
ab:93:26:ed:2b:7f:1a:74:a3:a8
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = NO, O = Buypass AS-983163327, CN = Buypass Class 2 CA 5
Validity
Not Before: Mar 11 09:40:43 2021 GMT
Not After : Sep 7 21:59:00 2021 GMT
Subject:
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:a5:1b:97:3e:d9:a4:6b:f9:84:dd:64:8c:41:c9:
83:f4:a2:ff:92:2c:fb:e7:71:80:4e:b2:d1:a0:73:
fb:66:5c:73:e3:73:f7:56:8c:b2:89:e0:0b:49:41:
6f:7b:3a:f8:69:76:96:95:eb:d3:df:90:96:27:51:
a8:7d:09:38:90:b1:46:d0:a5:4a:ef:fb:2a:49:50:
28:11:30:51:78:e8:50:d6:5c:3b:f1:83:24:5e:fc:
68:cf:eb:7b:e7:25:1f:b8:39:34:34:60:53:13:2d:
ca:25:93:13:48:4f:aa:f8:13:c1:78:ee:12:b9:47:
fc:a4:60:47:85:82:d5:c5:54:40:4c:3e:78:e8:21:
f9:f1:f5:95:23:9e:65:db:5d:8c:a9:ec:30:b8:42:
63:9e:c5:09:04:d8:4f:42:8f:9b:ec:63:d1:56:cd:
d6:1b:63:fc:1b:6a:f8:25:ea:27:40:4f:48:34:13:
8b:50:d0:ee:f8:c3:53:d0:b4:e1:3d:86:63:61:d6:
29:6b:ba:68:e1:0c:4b:3e:6c:4a:72:88:22:ca:fc:
af:4b:80:61:23:ae:0c:3b:b9:3a:90:72:67:02:cb:
e0:7b:5c:93:6e:0f:e8:58:ec:96:06:06:45:3d:6a:
c5:4e:49:3d:c0:80:92:6f:42:60:8a:68:91:59:02:
d5:ad
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Authority Key Identifier:
keyid:27:52:A4:6F:2D:2A:AB:40:93:90:EC:D6:69:CB:FE:7C:61:3B:7C:42
X509v3 Subject Key Identifier:
0C:B5:AB:AC:6B:71:CD:0B:AE:91:0D:ED:27:26:5B:B5:E2:31:86:9C
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Certificate Policies:
Policy: 2.16.578.1.26.1.2.7
Policy: 2.23.140.1.2.1
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.buypass.no/crl/BPClass2CA5.crl
X509v3 Subject Alternative Name: critical
DNS:test.cloudbool.com
Authority Information Access:
OCSP - URI:http://ocsp.buypass.com
CA Issuers - URI:http://crt.buypass.no/crt/BPClass2CA5.cer
CT Precertificate SCTs:
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : F6:5C:94:2F:D1:77:30:22:14:54:18:08:30:94:56:8E:
E3:4D:13:19:33:BF:DF:0C:2F:20:0B:CC:4E:F1:64:E3
Timestamp : Mar 11 09:40:44.012 2021 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:45:02:20:50:6B:87:76:AA:25:AD:24:F7:DE:31:98:
DC:B2:33:A8:52:40:02:9E:61:07:50:10:11:55:AA:AE:
D4:B2:C4:B9:02:21:00:CF:55:E8:AC:27:44:89:ED:31:
16:8E:D2:2E:90:66:E1:06:F7:0B:A9:C9:31:2E:2B:35:
52:79:26:94:B1:5D:A5
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : 44:94:65:2E:B0:EE:CE:AF:C4:40:07:D8:A8:FE:28:C0:
DA:E6:82:BE:D8:CB:31:B5:3F:D3:33:96:B5:B6:81:A8
Timestamp : Mar 11 09:40:43.990 2021 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:46:02:21:00:91:CF:07:B0:4D:5A:10:E8:8F:FD:57:
0B:DD:06:27:DF:A6:B2:62:64:6B:B6:AD:FD:0A:90:47:
44:85:59:23:33:02:21:00:90:04:BE:12:29:16:07:9E:
CE:08:65:AD:58:F0:F5:23:32:FE:5B:C8:A6:33:03:0A:
B4:52:77:5D:ED:53:59:7F
Signature Algorithm: sha256WithRSAEncryption
15:08:ea:fa:4b:3b:6f:61:34:40:a3:b0:14:43:b5:28:73:00:
60:af:7e:7b:7c:60:2c:2e:4d:e1:aa:5a:f4:4d:ff:b5:80:31:
43:f5:6d:fa:25:3a:4f:01:1e:dc:97:f8:70:9e:41:83:de:21:
6d:ea:4f:48:9f:ce:9c:a9:e1:46:fb:8a:4c:1a:56:54:a8:0e:
1a:90:da:bf:33:66:96:9e:5d:bd:fe:92:f2:94:45:f3:58:bb:
ef:07:c4:9d:c8:e5:3f:a0:25:19:c4:1f:86:4b:a2:1c:4e:6e:
fe:f0:7b:31:31:53:0f:a6:52:11:cc:35:9c:0b:92:38:c7:46:
0b:8d:17:f4:eb:9f:e2:7f:33:95:39:97:e6:c3:31:6b:17:7e:
19:c7:43:ce:7a:81:79:49:b6:0f:a7:63:fc:86:6c:2a:e9:db:
27:ea:fb:19:03:df:dd:20:e4:ad:84:47:9b:05:c2:cb:81:e7:
ef:e0:ba:d9:d8:94:e6:ab:c0:da:88:d5:1f:f8:d8:05:75:ee:
92:77:2f:a8:d0:6a:29:28:6a:4d:5f:95:29:f1:d5:8a:e8:a8:
69:bc:32:33:81:c4:6d:6e:91:fb:c3:26:fd:8a:45:f3:70:87:
20:fb:af:c6:ea:01:54:4e:76:db:df:d7:67:f3:24:dd:91:1d:
3e:64:d6:35:d5:55:7f:36:ea:f2:df:eb:b5:9e:8f:fe:66:1b:
be:a9:38:b3:e2:4e:a8:dd:fd:06:66:d1:92:e4:f5:36:ff:93:
9d:ba:c7:54:c3:8b:c8:2b:b5:17:70:d4:da:db:41:45:f8:a6:
21:d4:af:14:54:37:eb:34:a8:f0:dc:f1:b2:b6:6d:44:b5:3c:
e6:19:61:30:a5:90:dc:e4:5d:66:0e:e1:b3:f1:e6:05:46:2e:
24:79:a0:d2:91:c3:e6:47:46:e3:f7:2c:5a:2b:9d:83:3e:68:
1d:e1:de:e2:fc:cc:8f:94:56:74:6d:11:af:74:6c:ab:8d:48:
56:dd:a8:01:ca:75:5a:84:1d:3d:3a:29:57:e9:41:cb:74:18:
24:e3:80:59:e2:41:6b:a4:db:82:cb:06:ce:7d:43:d0:d6:13:
c4:a5:51:e2:8c:5c:a6:2d:e0:61:2f:91:d7:c9:d2:e7:3e:aa:
2b:b2:43:c1:f6:53:2d:45:c8:aa:bc:71:83:1c:65:81:80:44:
8d:63:d5:9e:c2:13:8b:70:d4:13:a1:63:c3:61:a1:9e:4b:f1:
09:31:d5:15:4c:c4:a1:6e:76:a8:99:be:45:13:05:fc:87:7e:
6f:5a:05:8b:9f:31:10:dc:25:75:51:43:6e:ce:51:7c:88:3e:
52:fe:f7:4b:bb:7a:98:15BuyPass免费证书OCSP服务器
本来我都没指望BuyPass在国内附近有OCSP服务器的,但是经过我的实际测试,发现BuyPass的OCSP使用的是akamai的CDN服务器,电信网络过去竟然有一定概率分配到隔壁湾湾,如图:
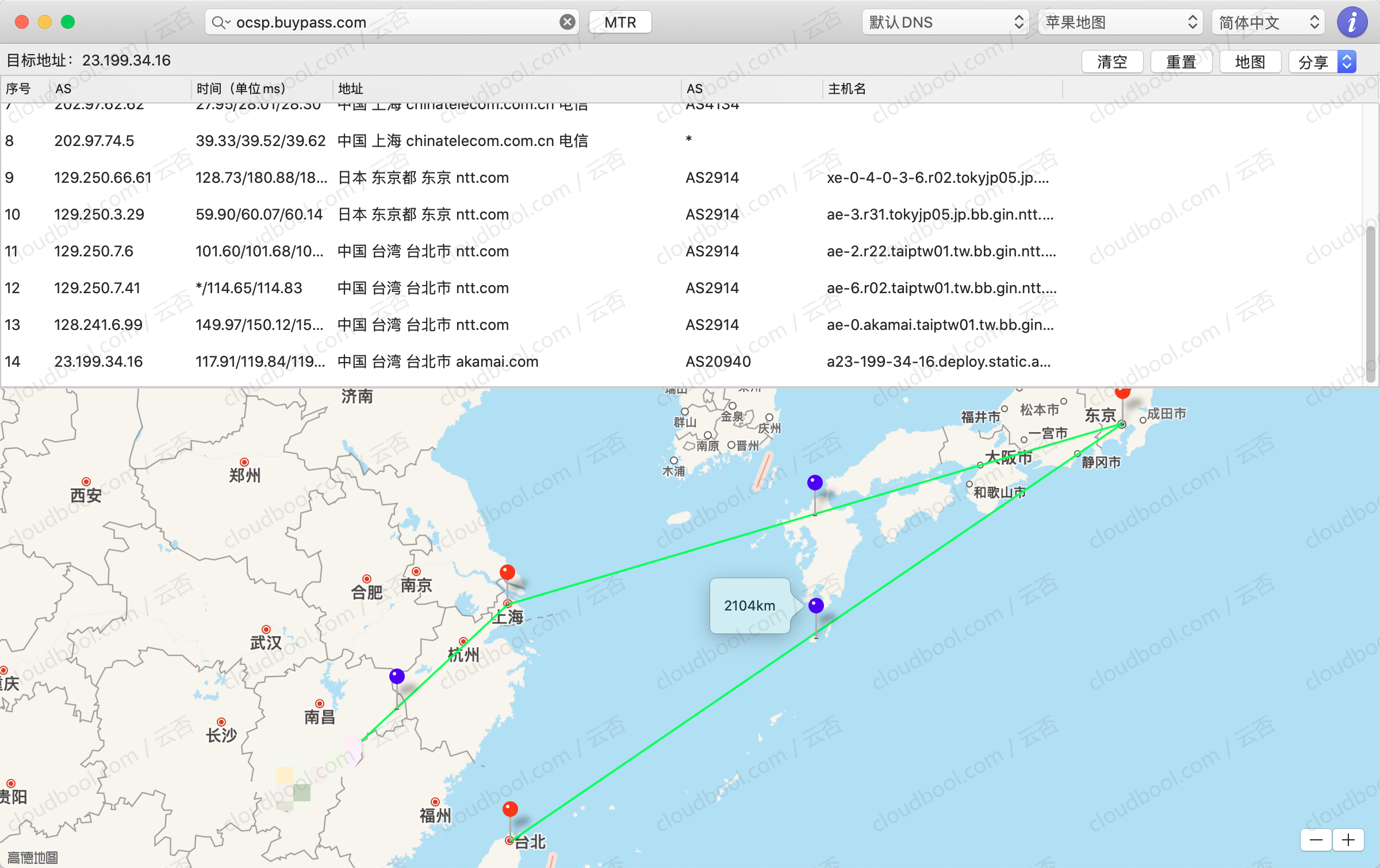
虽然在隔壁,但是有一定概率还是丢包的。
BuyPass免费证书兼容性
经过我在SSLLabs的测试,BuyPass的免费证书除了在XP系统下的IE8及以下版本的浏览器握手失败之外,其余各客户端都能正常兼容,兼容性还是不用担心的。
BuyPass免费证书使用小结
经过我的实际申请及使用体验,BuyPass的免费证书还是挺方便的,与letsencrypt相比各有优缺点,优点是证书有效期比letsencrypt的长,单次申请有效期为180天,缺点也有,BuyPass的免费证书不支持泛域名也就是wildcard,各有优劣了,对于单个服务想长期不管的,可以考虑上BuyPass,或者也可以配置自动更新,将BuyPass作为letsencrypt的一种替代。
相关文档:https://community.buypass.com/t/k9r5cx/get-started